Hackers alleged they have client documents and court details belonging to a Sydney law firm, but its principal said only a limited amount of data was accessed.
The Akira ransomware gang has claimed it has successfully hacked a Sydney law firm that specialises in immigration matters and is threatening to publish a raft of sensitive information online, Cyber Daily reported.
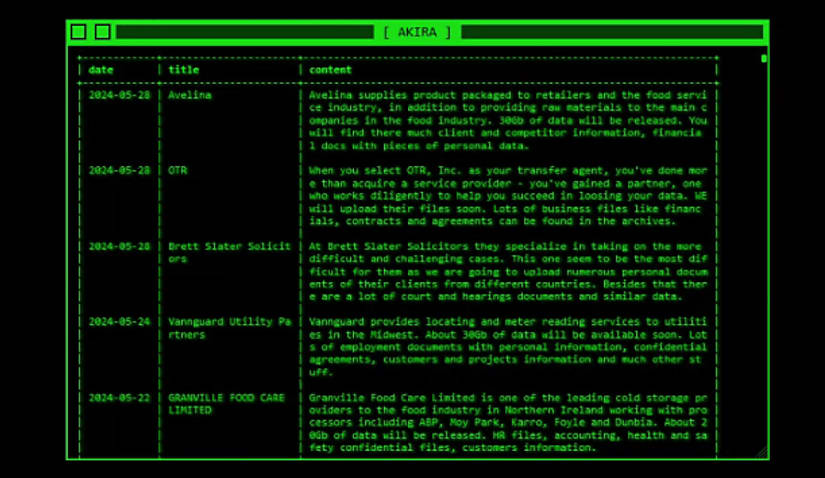
“At Brett Slater Solicitors they specialise in taking on the more difficult and challenging cases,” Akira said in its leak site post.
“This one seem [sic] to be the most difficult for them as we are going to upload numerous personal documents of their clients from different countries. Besides that, there are a lot of court and hearings documents and similar data.”
Brett Slater is linked to Harbourside Legal Services, which operates out of the same North Sydney address.
The firm offers a range of immigration-related services, including assisting in acquiring visas, citizenship applications, and any appeals if a visa has not been granted.
Abraham Ishkhanian, principal of Harbourside Legal, said the “majority of our data is very safe” and protected by LEAP’s software.
Only a very limited amount of data in Microsoft’s OneDrive was accessed.
“Our IT team has looked at our whole systems and have increased protections.
“We had three levels of protection before, now we have five.
“They are still trying to identify how exactly they got into the system, they haven’t been able to until now, but they are looking into it.”
The firm has removed the PC that was accessed and the server that handles the logins.
They are assisting with ongoing investigations.
Akira operates on the TOR network, or the dark web, and is known to post details of its victims and the leaked data if their ransom demand is not responded to.
As a rule, Akira does not post proof of its hacks but has published the data of many of its victims in the past, and there is little doubt it will do the same again. The gang has also not posted details of any ransom deadline.
“Well, you are here. It means that you’re suffering from cyber incident right now. Think of our actions as an unscheduled forced audit of your network for vulnerabilities. Keep in mind that there is a fair price to make it all go away,” the gang said to all visitors to its retro black and green leak site.
“Do not rush to assess what is happening – we did it to you. The best thing you can do is to follow our instructions to get back to your daily routine, by cooperating with us you will minimise the damage that might be done.”
Since it formed in May 2023, Akira has claimed more than 250 victims and has been the subject of an FBI advisory.